Wednesday, September 7, 2016
Xolo Era 1X Works With the Reliance Jio Network Launched at Rs 4,999
Xolo Era 1X Works With the Reliance Jio Network, Launched at Rs. 4,999
After introducing the Xolo Era X in February, the company has expanded its Era series and introduced the successor Era 1X in India. Xolo has launched its new 4G VoLTE smartphone under its Era series, which is named as Xolo Era 1X. The smartphone is priced at Rs 4,999 and will be offered exclusively through Flipkart from September 15. Interested customers can register on Xolo’s official website and they will stand a chance to win a Xolo Era 1Xsmartphone. The Era 1X comes in gunmetal, black, gold and brown color options.
About Mandvi Dwivedi
RELATED POSTS
The Secret Behind Deleting You Need To Know
Recovering Files
Mobile Devices
Deleting Files
Image source
About iGadgetware iGW
RELATED POSTS
FREE DDoS Handbook: The Ultimate Guide to Everything You Need to Know About DDoS Attacks
DDoS Handbook: The Ultimate Guide to Everything You Need to Know About DDoS Attacks.
DDoS attacks are the most persistent and damaging cyber-attacks. They reflect hackers’ frustratingly high levels of tenacity and creativity – and create complex and dynamic challenges for anyone responsible for cyber security.
Long Description: While cyber-threats are by nature a moving target, Radware’s DDoS Handbook offers expert advice, actionable tools and tips to help detect and stop DDoS attacks.
Read it to understand:
- Brief history of DDoS attacks, plus roundup of recent cyber-attacks
- Overview of major attack categories, specific attack types and tools
- What lies ahead: predictions for 2015 and beyond
- Things to consider when planning for cyber-attacks
- Protecting enterprise assets in the cloud
Tuesday, September 6, 2016
LuaBot First Botnet Malware To Target Linux Platforms
 |
| View the binary’s ASCII in the last part and you’ll see the first email address | Credit: MalwareMustDie |
Researchers Finds LUA Language ELF Compiled Malware Called As Linux/LuaBot.
Trojan coded in Lua to target linux Platforms to adding into a Botnet explain by security researcher from MalwareMustDie.
The code is interacted with the udp.lua, as per its name suggesting a lua library of User Datagram Protocol function and struct, This is showing the malware has its own lua resolver code for the DNS query, and has ability to form its own UDP packet to be sent to any destination.
There’s also the telnet.lua codes compiled in this ELF, which is after being reversed it seems to be a simple telnet basic communication functions interpreted in lua language (that can be found many references in the internet) that may allow Linux/LuaBot to communicate remotely through this protocol.
What is LUA?
According to Softpedia,
At the moment, the LuaBot trojan is packed as an ELF binary that targets ARM platforms, usually found in embedded (IoT) devices. Based on his experience, this seems to be the first Lua-based malware family packed as an ELF binary spreading to Linux platforms.
Get Your Business Ready to Get Paid
Get Your Business Ready to Get Paid.
About iGadgetware iGW
RELATED POSTS
Lenovo A Plus, Lenovo P2 Smartphones Launched at IFA 2016
Lenovo A Plus, Lenovo P2 Smartphones Launched at IFA 2016
Lenovo hasn’t stopped until now even after the K6 family of devices was introduced. Now Lenovo has taken another step and bought two new devices – The Lenovo P2 and A Plus with different specifications. Lenovo has been busy this year, with launched of many devices and this Chinese multinational technology is also known for its wide range of Notebooks, ThinkPads, and Laptops. Newly you have also seen that Lenovo and Microsoft have signed a new joint agreement by which few selected Android-powered Lenovo and Motorola devices will come pre-loaded with Microsoft-created applications like Office, OneDrive, and Skype.
About Mandvi Dwivedi
RELATED POSTS
Monday, September 5, 2016
Ganesh Chaturthi 2016: Twitter Launches Special Emojis
Ganesh Chaturthi 2016: Twitter launches special emoji
This year, Twitter joins the festive fervor by introducing a special Lord Ganesha Twitter emoji that Indians can Tweet to welcome the much-loved god home on Monday, 5th September. When people Tweet using #HappyGaneshChaturthi, #GaneshChaturthi, #गणेशचतुर्थी, #Ganeshotsav, #गणेशोत्सव, a Lord Ganesha emoji will be started next to the hashtag. The emoji has gone live since September 4 and will be active until the last day of celebrations September 16.
About Mandvi Dwivedi
RELATED POSTS
Reliance Jio Will Also Give Unlimited Data on Plan Rs. 149
Reliance Jio Will Also Give Unlimited Data on Plan Rs. 149
Today Reliance Jio is set to roll out its full-fledged 4G services in India. That means that Jio services will be open to all smartphone brands, which were not under its umbrella previously. Though Reliance Industries Limited (RIL) opened its 4G service to most brands like LG, Samsung, Asus, HTC,Lava, Micromax etc.; there still were a few left out. This includes Xiaomi, iPhone, Motorola, and Lenovo. Now, any user with a 4G-enabled handset is appropriate for Jio SIM card.
About Mandvi Dwivedi
RELATED POSTS
Sunday, September 4, 2016
5 Things Only People That Have Kids That Use Up All Their Broadband Will Understand
5 Things Only People That Have Kids That Use Up All Their Broadband Will Understand.
About iGadgetware iGW
RELATED POSTS
Saturday, September 3, 2016
Betabot Trojan Steals Your Passwords And Install Ransomware To Monetize
Betabot Trojan Steals Your Passwords And Install Ransomware To Monetize.
Betabot was delivered by Neutrino Exploit Kit. The IP used for both Betabot and Cerber is 93[.]174.91.49. A virustotal report on this IP provides additional details here. A screenshot below highlights the multiple filenames used between Betabot and Cerber. Invincea described in its blog,
 |
| Server IP used to download Betabot and Cerber malware |
You can see in image Betabot weaponized documents have been found bb.exe (bb denoting betabot), bbcrypt.exe, and diablo.exe.
How this attack work?
Betabot spread through spam emails contained a file attachment, a Word file contain malicious macro scripts. In Microsoft office user activated macro support then scripts automatic download and install Betabot to infect your computer. And then scrapes all passwords stored in all local browsers.
According to report of Invincea, Cyber attacker maximizing the profits from an endpoint compromise, earning much larger payout by using multiple attack techniques.
Conclusion:
- Never open unknown file attachment in Email.
- Beware from Social Engineering attack.
Friday, September 2, 2016
Your Business: The First Year
Your Business: The First Year
So you’ve finally done it. The lease for the property has been signed and you’ve got a base to operate from. Now where do we go from here?
About iGadgetware iGW
RELATED POSTS
Facebook And Twitter Accounts Can Hack Through target=”_blank” Vulnerability
Facebook And Twitter Accounts Can Hack Through target=”_blank” Vulnerability.
The target=”_blank” is using for target attribute specifies where to open the link in new tab. Hackers are using this trick for Phishing Attack. When a user click on the text link, then the malicious link will open in new Tab. This cyber attack could happen on browser based not Web Servers.
How does it work?
According to security researcher Ben Halpern, Facebook and Twitter social networks accounts are vulnerable.
In order to restrict the behavior window.opener access, the original page needs to add a rel=”noopener” attribute to any link that has target=”_blank”. However, Firefox does not support that tag, so you should actually use rel=”noopener noreferrer” for full coverage.
Some amount of prevention can be achieved through scripting, though, as observed with Twitter, this seems to fail on Safari. This issue is not well-known, and is totally underestimated. This has been brought up in a Web Hypertext Application Technology Working Group mailing list, said Halperm.
How to Fix?
Developers should add attribute rel=”noopener” into the website code. Because some browsers does not fully support that attribute, developers should use rel=”noopener noreferrer” instead.
Intel Launches 7th-Generation ‘Kaby Lake’ Core Processors For Laptops
Intel Launches 7th-Gen ‘Kaby Lake’ Core Processors For Laptops and 2-in-1s
Intel has officially introduced its first wave of 7th-generation Core processors, well known by their codename Kaby Lake. Today’s launches are CPUs in the U and Y series, which are planned for thin and light portables such as notebooks and 2-in-1s. Processors for mainstream and enthusiast desktop PCs, workstations, beefier laptops, and other kinds will be refreshed early next year.
About Mandvi Dwivedi
RELATED POSTS
New MacBook Pro, MacBook Air, 5K Monitor Going To Launch In October 2016
New MacBook Pro, MacBook Air, 5K Monitor Going To Launch In October 2016
Apple is planning a more expensive refresh of its Mac portfolio, with new MacBook Air and iMac models on the way, and they could come to as soon as October, as per the new report. Apple is introducing the next iPhone on September 7. The Cupertino giant is also likely to introduce the successor of the original Apple Watch, but there’s been no word on Apple’s strategies for its other products alongside. Now, we get fresh intelligence appealing that Apple is looking to bring new Macbooks and a new 5K display sometime in October. Apple is also working on few iPad upgrades that are probable to be rolled out next year.
Video:
About Mandvi Dwivedi
RELATED POSTS
Thursday, September 1, 2016
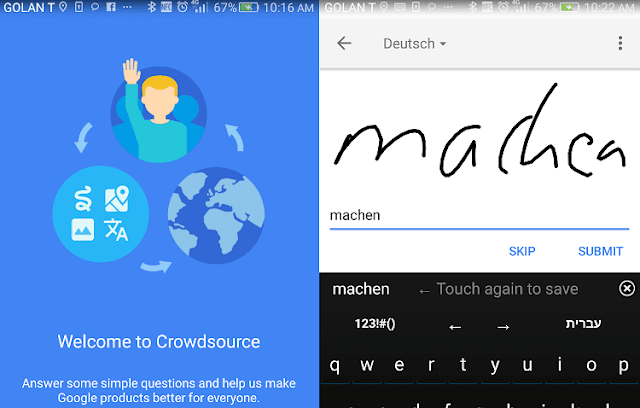
Google’s Crowdsource App Ask Your Help For Transcriptions and Translations
Google’s Crowdsource App Ask Your Help for Transcriptions and Translations.
Google is watching to users for helping out with one of the most irritating tasks on the web. Crowdsource is a new app that asks users to translate and transcript text or images. Crowdsource has quietly looked on Google Play, asking users to do brief tasks that will help improve the quality of Google services like translation, Maps, image transcription, and more.
About Mandvi Dwivedi
RELATED POSTS
Moto E3 Power Smartphone With 3500mAh Battery Goes on Sale
Moto E3 Power SmartphoneWith 3500mAh Battery Goes on Sale
In July Motorola revealed the Moto E3 smartphone revealing a few specifications, a price tag of GBP 99, and early September accessibility in the UK. Now, a variant called the Moto E3 Power has gone on sale by a third-party retail site in Hong Kong – with no official declaration for it yet. As the name advises, the smartphone comes with a better battery, and it also bears a few upgrades to other specifications and sells at a price tag of HKD 1,098 (roughly Rs. 9,500).
About Mandvi Dwivedi
RELATED POSTS
Wednesday, August 31, 2016
Hack QR Code Through QRLJacking Attack
Hack QR Code Through QRLJacking Attack
QRLJacking or Quick Response Code Login Jacking is a simple social engineering attack vector capable of session hijacking affecting all applications that rely on “Login with QR code” feature as a secure way to login into accounts. In a simple way, In a nutshell victim scans the attacker’s QR code results of session hijacking. This tool is launched by Information Security Researcher Mohamed Abdelbasset Elnouby from Seekurity Labs.
What are the requirements to achieve a successful QRLJacking attack?
QRLJacking attack consists of two sides:
- Server Side: A server side script is needed to serve and shape the final look to the victim.
- Client Side: Cloning the QR and pushing it to the phishing page.
Example: WhatsApp Web Application!
Server Setup (Attacker’s hosting):
Upload “qrHandler.php” to your server, this php file is used to convert the base64 qr code string into a valid .JPG file
Now we have a valid generated QR image named “tmp.jpg” residing in the same root folder of your files and will be updated whenever that php file will be called, So we can put it anywhere “for example a fake WhatsApp page, a scam page with an offer related to WhatsApp, etc… depending on your creativity”
Now update the “phishing.html” file your prefered phishing page source code.
Client Side Setup (Attacker’s browser):
- Open your Firefox browser!
- Write “about:config” in the url area, click the “i’ll be careful, i promise” confirmation button.
- Search for a preference named “security.csp.enable” and change it’s value to “false” by double clicking it to allow performing an XHR Request over a different domain (We’re not supporting leaving this preference disabled, you may do that while testing, but after that you should set the preference to its original state).
- Instal Greasemonkey addon (https://addons.mozilla.org/en-US/firefox/addon/greasemonkey) and be sure that the module file “WhatsAppQRJackingModule.js” is loaded and already running!
- Now We’re Ready, Browse to our example “https://web.whatsapp.com” on your side, Wait for a WhatsApp session to be loaded, Greasemonkey should now inject our WhatsApp module file to catch and .
- Send the direct link of the final phishing page to a victim “Once the QR scanned, Victim’s session is yours now”
Video:
Attacking WhatsApp Web Application and performing MiTM attack to inject a bogus ad including WhatsApp QR Code Demo Video.